Security PSA: High Severity Plugin Vulnerability
There is a high severity vulnerability present in a commonly used WordPress plugin. If you believe your account was compromised or you were affected by this vulnerability already, please notify us immediately at support@reclaimhosting.com.

PSA: There is currently a high severity vulnerability in a widely used WordPress plugin. This vulnerability was reported to WordFence Intelligence and is assigned CVE-2023-6846, discovered by Tobias Weißhaar. The File Manager Pro plugin is vulnerable to Arbitrary File Upload in all versions up to, and including, 8.3.4 via the mk_check_filemanager_php_syntax AJAX function. Due to this, users with subscriber access and above are able to execute code on the server. Version 8.3.5 introduces a capability check that prevents users lower than admin from executing this function.
As described by the WordFence team:
"The function creates the temp file, and puts the php code in it. After that, it executes a syntax check only, which is completely safe as it is not possible to execute the code.
But the temp file is not deleted immediately. Theremove_fm_temp_file()function deletes the temp file, which is added to theadmin_inithook, but it only runs when the admin page is reloaded. This means there is a period of time where the test file lives on the server before it is deleted, making it accessible to a threat actor.
Unfortunately no capability checks were used in the vulnerable versions, there is only a check to verify that the user is logged in to WordPress, and the temp file is not immediately deleted either. This means that any logged in user, such as a subscriber, can add any PHP code to the temp file and subsequently access it. This makes it possible for attackers to upload arbitrary malicious PHP code and then access the file to trigger remote code execution on the server."
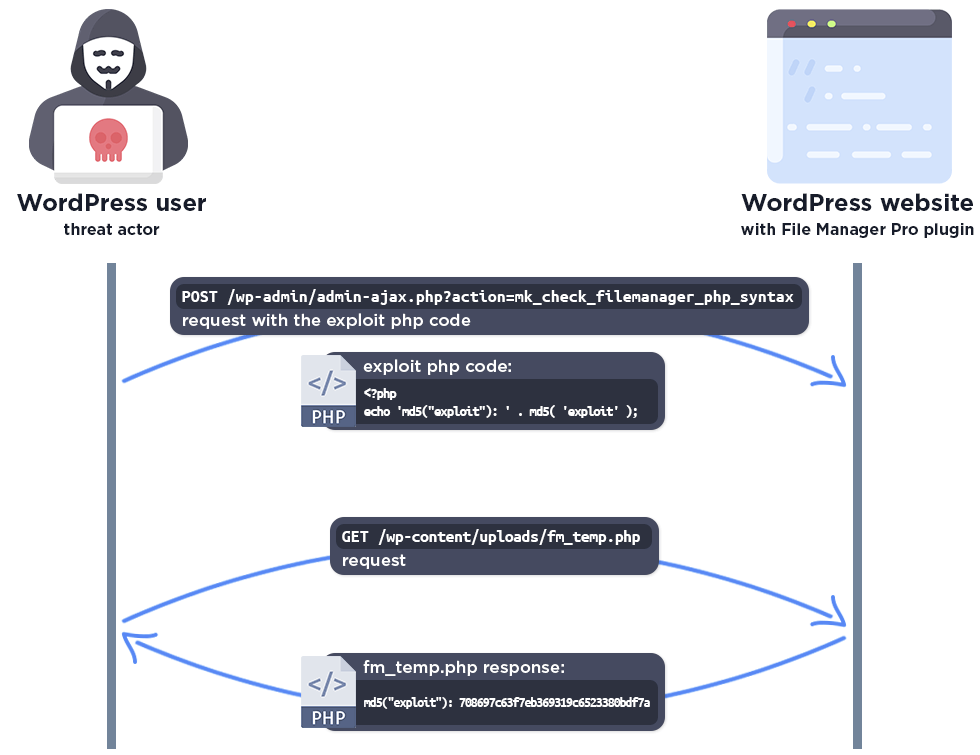
Due to this being an extremely high severity vulnerability allowing malicious individuals with minimal permissions to execute malicious code on the server, we recommend updating the File Manager Pro plugin immediately. If you believe this vulnerability has already been exploited on your install, please contact support@reclaimhosting.com immediately.
View the original WordFence blog post here: