Security PSA: New Phishing Campaign
There is currently an on-going phishing campaign targeting WordPress users. If you believe your account was compromised or you were affected by this campaign already, please notify us immediately at support@reclaimhosting.com.

PSA: There is currently an on-going phishing campaign targeting WordPress users. This campaign was discovered by the threat intelligence team at WordFence Security and is fairly widespread already. You can view an example of one of these emails below:
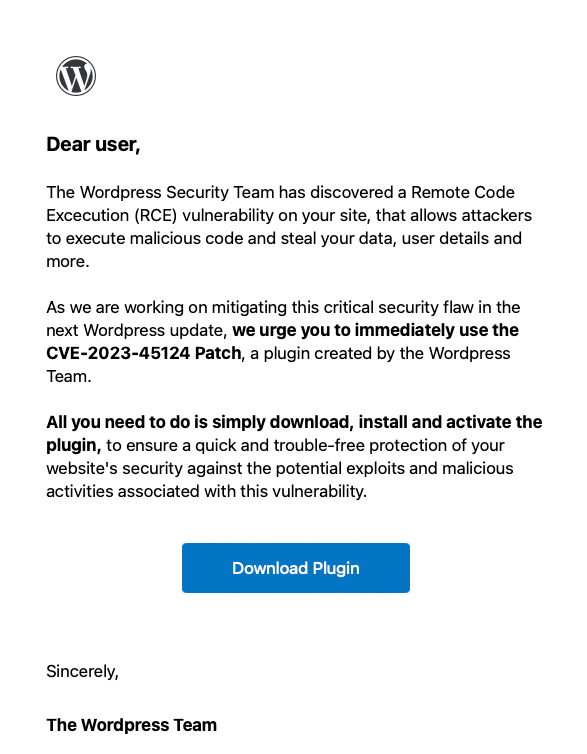
As you can see, this email is masquerading as a legitimate email from the WordPress Team, and also advertises a patch for a critical CVE (CVE-2023-45124). This CVE does not exist. If clicked, the user is taken to a fraudulent plugin page on en-gb-wordpress.org. As described by the WordFence team:
"If the victim downloads the plugin and installs it on their WordPress site, the plugin is installed with a slug ofwpress-security-wordpressand adds a malicious administrator user with the usernamewpsecuritypatch. It then sends the site URL and generated password for this user back to a C2 domain:wpgate[.]zip. The malicious plugin also includes functionality to ensure that this user remains hidden. Additionally, it downloads a separate backdoor fromwpgate[.]zipand saves it with a filename ofwp-autoload.phpin the webroot. This separate backdoor includes a hardcoded password that includes a file manager, a SQL Client, a PHP Console, and a Command Line Terminal, in addition to displaying server environment information...This allows attackers to maintain persistence through multiple forms of access, granting them full control over the WordPress site as well as the web user account on the server."
A couple indicators that your account has been compromised, as listed by the WordFence team:
- A
wp-autoload.phpfile in the webroot with a SHA-256 hash offfd5b0344123a984d27c4aa624215fa6452c3849522803b2bc3a6ee0bcb23809 - A plugin with a slug of wpress-security-wordpress
- A hidden administrative user with a username of
wpsecuritypatch - The following malicious domains:
en-gb-wordpress[.]orgwpgate[.]zip
If you believe your account was compromised or you were affected by this campaign already, please notify us immediately at support@reclaimhosting.com
View the original WordFence blog post here:






